| CPC H04L 63/1491 (2013.01) [H04L 63/102 (2013.01); H04L 63/1425 (2013.01); H04L 63/20 (2013.01)] | 20 Claims |
|
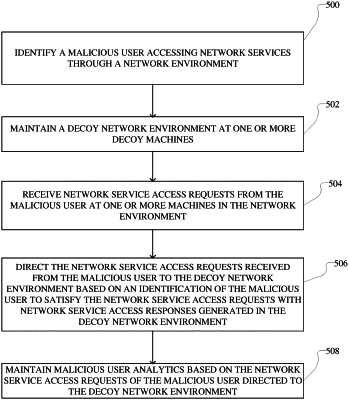
1. A method, comprising:
identifying a malicious user accessing network services through a network environment associated with an enterprise based on a signature of a previously identified malicious user, wherein the signature of the previously identified malicious user includes one or more patterns of network service access requests and responses of the previously identified malicious user in one or more previous attacks, the signature being refined over time based at least in part on previous interactions with a decoy network environment;
receiving network service access requests from the malicious user in interacting with the network environment associated with the enterprise;
directing the network service access requests received from the malicious user to the decoy network environment in response to identifying the malicious user based on the signature of the malicious user; and
maintaining malicious user analytics based on the network service access requests of the malicious user directed to the decoy network environment.
|