| CPC H04L 63/1491 (2013.01) [H04L 63/0263 (2013.01); H04L 63/08 (2013.01); H04L 67/141 (2013.01)] | 15 Claims |
|
1. A method, comprising:
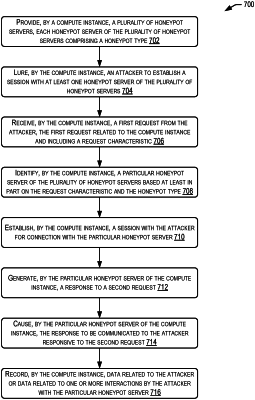
providing, by an Infrastructure-as-a-Service (IaaS) compute instance executed by a controller of an IaaS service provider, a plurality of honeypot servers, each honeypot server of the plurality of honeypot servers comprising a honeypot type, the controller being hosted by a third-party service provider outside of an IaaS servicer provider environment;
exposing, by the compute instance, one or more ports to a public network to lure an attacker to establish a session with at least one honeypot server of the plurality of honeypot servers;
receiving, by the compute instance, a first request from the attacker, the first request related to the instance and including a request characteristic;
identifying, by the compute instance, a particular honeypot server of the plurality of honeypot servers based at least in part on the request characteristic and the honeypot type;
establishing, by the compute instance, a session with the attacker for connection with the particular honeypot server;
generating, by the particular honeypot server of the compute instance, a response to a second request associated with a function of the honeypot server from the attacker, the response to the second request generated by the third-party service provider and being configured to appear to be from the IaaS service provider;
causing, by the particular honeypot server of the compute instance, the response to be communicated to the attacker responsive to the second request; and
recording, by the compute instance, data related to the attacker or data related to one or more interactions by the attacker with the particular honeypot server.
|