| CPC H04L 63/1433 (2013.01) [H04L 63/1425 (2013.01); H04L 63/1458 (2013.01)] | 18 Claims |
|
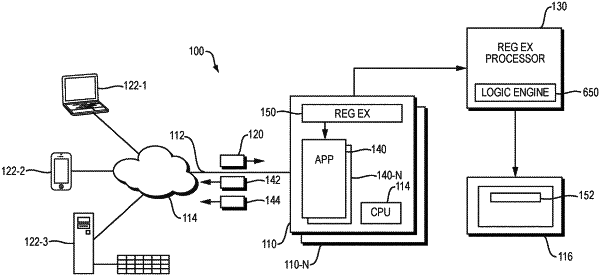
1. A method for assessing a regular expression for vulnerability to ReDoS attacks, comprising:
receiving a regular expression, the regular expression for evaluating a string defined by an ordered set of characters from an alphanumeric input device;
evaluating the regular expression for determining if a parsing operation of the string according to the regular expression results in a disproportionate resource consumption, evaluating further comprising:
identifying loop constructs in the regular expression;
determining if the loop constructs define a loop within a loop, each loop having a self transition based on a transition value in common with the other loop; or
determining if the loop constructs define a first loop, followed by a bridge, followed by a second loop, the bridge denoted by a transition value in common with at least one of the first loop or second loops, further comprising, for each of the identified loop constructs:
generating a logic equation representation of the loop construct; solving the logic equation to identify a satisfying string expression;
returning the satisfying string expression as an indication of vulnerability of the regular expression, or
if no satisfying expression is returned by an SMT (Satisfiable Modulo Theories) analysis, return that no indication of vulnerability exists;
determining, based on the evaluation, if the resource consumption constitutes a Regular Expression Denial of Service (ReDoS) attack; and if so,
rendering the indication of vulnerability of the regular expression.
|