| CPC H04L 63/1425 (2013.01) [H04L 43/045 (2013.01); H04L 43/08 (2013.01); H04L 63/1433 (2013.01); G06F 21/577 (2013.01)] | 13 Claims |
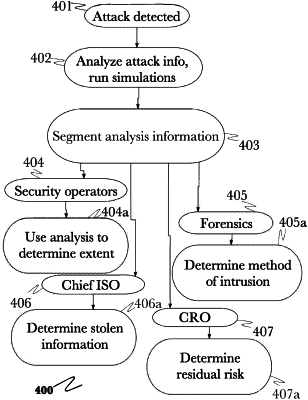
|
1. A system for comprehensive data loss prevention and compliance management, comprising:
a computing device comprising a processor and a memory;
an observation and state estimation module comprising a first plurality of programming instructions stored in the memory and operating on the processor, wherein the first plurality of programming instructions, when operating on the processor, cause the computing device to:
monitor a plurality of connected resources on a network; and
produce a cyber-physical graph representing the plurality of connected resources, wherein:
the connected resources comprise one or more of people, devices, systems, and organizations within the network;
the cyber-physical graph comprises nodes representing the connected resources, which each node having one or more properties containing descriptive information for the connected resource represented by that node; and
the cyber-physical graph comprises edges representing the logical relationships between the plurality of connected resources and the physical relationships between any connected resources comprising a hardware device;
an activity monitoring engine comprising a second plurality of programming instructions stored in the memory and operating on the processor, wherein the second plurality of programming instructions, when operating on the processor, cause the computing device to:
generate expected behavior data of the connected resources within the network by applying a behavioral model to each node of the cyber-physical graph;
generate actual behavior data of the connected resources within the network from time-series data comprising a record of network events and the respective times at which each network event occurred;
detect deviations of the actual behavior data from the expected behavior data by comparing the expected behavior data properties of each node with the actual behavior properties of that node; and
when deviations are detected, send information about the deviation to a risk analysis and scoring engine; and
the risk analysis and scoring engine comprising a third plurality of programming instructions stored in the memory and operating on the processor, wherein the third plurality of programming instructions, when operating on the processor, cause the computing device to:
receive deviation information from the activity monitoring engine;
analyze the severity of a threat posed by the deviation using at least one analysis algorithm; and
generate a risk score based on a plurality of factors which indicate the severity of the threat.
|