| CPC H04L 63/1416 (2013.01) [G06F 16/183 (2019.01); G06F 21/552 (2013.01); G06F 21/554 (2013.01); G06F 21/604 (2013.01); G06F 21/6218 (2013.01); H04L 63/104 (2013.01); H04L 63/105 (2013.01); H04L 63/107 (2013.01); H04L 63/108 (2013.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01); H04L 67/535 (2022.05)] | 26 Claims |
|
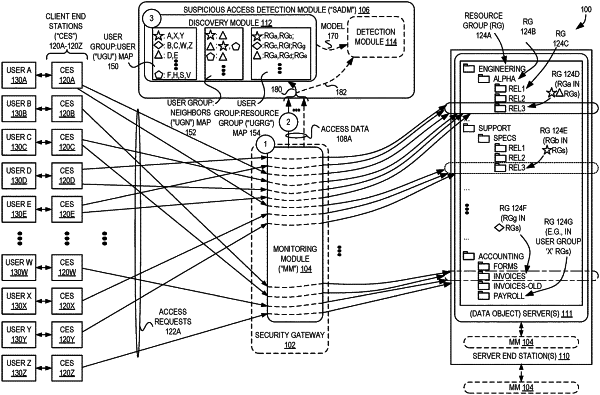
1. A method by one or more computing devices to detect suspicious access requests seeking access to different ones of a plurality of data objects, the plurality of data objects being organized within a plurality of resource groups, the method comprising:
determining, based on a first access data describing a plurality of access requests sent on behalf of a plurality of users, the following:
a first set of one or more accessed resource groups, for each respective one of the plurality of users, that identifies those of the plurality of resource groups that include those of the data objects to which access is sought by the access requests sent on behalf of the respective one of the users,
a plurality of user groups determined based on similarities between the first sets of accessed resource groups of the plurality of users,
a second set of resource groups, for each respective one of the plurality of user groups, that identifies those of the plurality of resource groups in the first sets of accessed resource groups determined for the respective ones of the users in the respective one of the user groups, and
for each of the plurality of user groups, which of the others of the plurality of user groups are considered nearby that user group based on a level of commonality between the second sets of resource groups determined for the respective ones of the user groups;
determining, based on a second access data describing at least a first access request, that the first access request is suspicious, wherein the first access request seeks access to a first data object of the plurality of data objects and was issued on behalf of a first user of the plurality of users, wherein the first user is determined to belong to a first user group of the plurality of user groups, wherein the determining that the first access request is suspicious includes determining that the first data object is included in a first resource group of the plurality of resource groups and that the first resource group is not within the respective second sets of resource groups determined for the first user group and those of other user groups determined to be nearby the first user group; and
causing an alert to be generated responsive to the first access request being determined to be suspicious.
|