| CPC H04L 63/1416 (2013.01) [G06N 5/04 (2013.01); H04L 63/145 (2013.01); H04L 63/1408 (2013.01); H04L 63/1433 (2013.01); H04L 63/0227 (2013.01)] | 20 Claims |
|
1. A method for guiding a response to a security incident, comprising:
monitoring a plurality of occurrences in a computer system, wherein the plurality of occurrences includes (1) a first occurrence whereby a first file instantiates a first process that creates or registers a second file, and (2) a second occurrence whereby the computer system instantiates a second process from the second file;
determining, based on adjacency data, that at least a subset of the plurality of occurrences is relevant to the second process, wherein the subset includes the first occurrence and the second occurrence, wherein the adjacency data includes data indicating relevance of the first occurrence to the second occurrence;
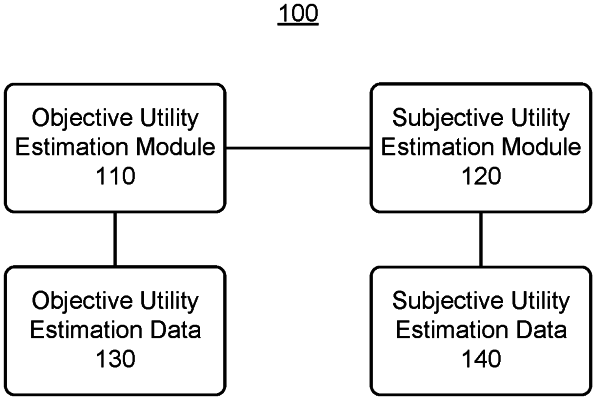
estimating a respective utility of investigating each occurrence in the subset;
selecting two or more occurrences from the subset based, at least in part, on the estimated utilities, the selected occurrences including the first occurrence and the second occurrence; and
guiding the response to the security incident at least by presenting, to a user, data corresponding to the selected occurrences.
|