| CPC H04L 63/1416 (2013.01) [G06F 16/2468 (2019.01); G06F 16/258 (2019.01); G06F 16/955 (2019.01); G06N 7/01 (2023.01)] | 17 Claims |
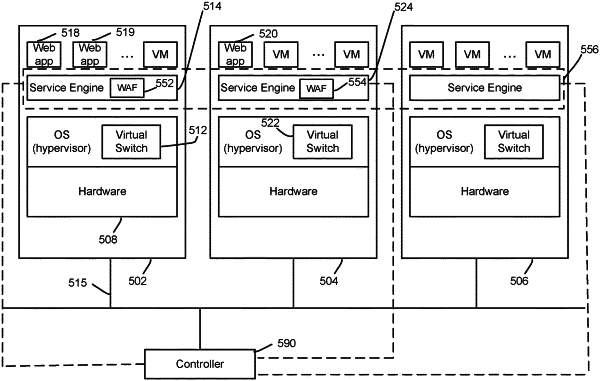
|
1. A method of performing firewall operations for a network based on a dynamic categorization of parameters stored in received packets, the method comprising:
receiving a first packet comprising a uniform resource identifier (URI) that includes a parameter;
generating a plurality of tokens from the parameter; and
computing a compound probability by aggregating component probability computed for each generated token in the plurality of generated tokens, wherein the compound probability expresses whether the plurality of generated tokens is associated with an attack on the network, wherein said computing the compound probability comprises computing the compound probability from a set of one or more probabilities that were computed previously for sets of one or more prior tokens each set of which (i) is generated for a received prior packet and (ii) is similar to the plurality of generated tokens,
wherein a first component probability for a first generated token is computed from a set of one or more probabilities that were computed previously for a first set of one or more prior tokens each of which (i) is generated for a packet received prior to the first packet and (ii) is similar to the first token,
wherein a second component probability for a second generated token is computed from a set of one or more probabilities that were computed previously for a second set of one or more prior tokens each of which (i) is generated for a packet received prior to the first packet and (ii) is similar to the second token.
|