| CPC H04L 63/101 (2013.01) | 24 Claims |
|
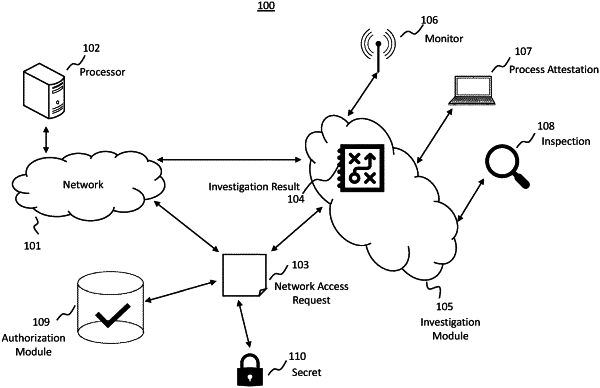
1. A non-transitory computer readable medium including instructions that, when executed by at least one processor, cause the at least one processor to perform operations for securely handling secrets within a development and operations pipeline, the operations comprising:
identifying a network access request for a process within the development and operations pipeline;
accessing a result of at least one investigation, wherein the at least one investigation includes at least one of:
monitoring the process behavior,
performing a process attestation, or
performing an inspection of the network access request;
determining, based on the result of the at least one investigation, whether to authorize the network access request; and
conditional on whether the network access request is authorized, dynamically injecting a decrypted or unencrypted secret into the network access request, wherein the secret is not made available to the process itself and the secret is encrypted after the injection.
|