| CPC H04L 63/0457 (2013.01) [H04L 9/065 (2013.01); H04L 9/14 (2013.01); H04L 9/3073 (2013.01); H04L 9/3242 (2013.01); H04L 63/0435 (2013.01); H04L 63/166 (2013.01)] | 31 Claims |
|
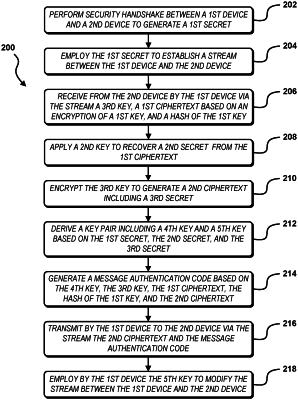
1. A computer-implemented method for secure network communication in a communication session, the computer-implemented method comprising:
performing by a first device a security handshake between the first device and a second device to generate a first secret;
employing by the first device the first secret to establish a stream between the first device and the second device;
receiving from the second device by the first device via the stream a third key, a first ciphertext based on an encryption of a first key, and a hash of the first key;
applying a second key to recover a second secret from the first ciphertext;
encrypting the third key to generate a second ciphertext comprising a third secret;
deriving a key pair comprising a fourth key and a fifth key based on the first secret, the second secret, and the third secret;
generating a message authentication code based on the fourth key, the third key, the first ciphertext, the hash of the first key, and the second ciphertext;
transmitting by the first device to the second device via the stream the second ciphertext and the message authentication code; and
employing by the first device the fifth key to modify the stream between the first device and the second device.
|