| CPC H04L 63/0428 (2013.01) [H04L 9/0819 (2013.01); H04L 9/0894 (2013.01); H04L 9/14 (2013.01); H04L 45/00 (2013.01); H04L 63/0227 (2013.01); H04L 63/105 (2013.01); H04L 69/22 (2013.01); H04L 63/126 (2013.01)] | 20 Claims |
|
1. A method, comprising:
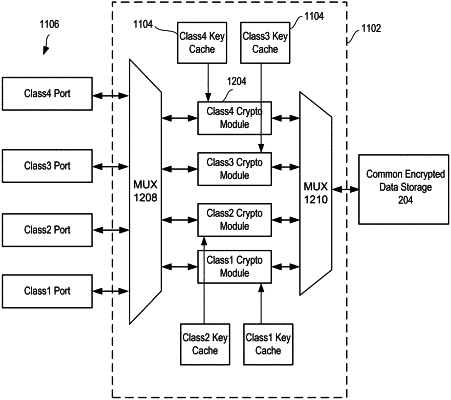
receiving, by a first computing device on a first port of a plurality of ports, a data packet, wherein each of the ports corresponds to one of a plurality of security classes including a first security class that corresponds to the first port, and the first computing device comprises a plurality of cryptographic modules each dedicated to one of the plurality of security classes;
routing, based on at least one header, the data packet to a first cryptographic module of the plurality of cryptographic modules of the first computing device, the first cryptographic module of the first computing device being dedicated to the first security class;
encrypting the data packet using the first cryptographic module;
tagging the data packet using tagging data that identifies the first security class and the first port;
outputting the encrypted data packet to a first data storage;
transmitting the encrypted data packet from the first data storage to a second data storage;
receiving, by a second computing device, the encrypted data packet from the second data storage, wherein the second computing device comprises a plurality of cryptographic modules each dedicated to one of the plurality of security classes;
selecting, based on the tagging data, one of the plurality of cryptographic modules of the second computing device; and
decrypting, using the selected cryptographic module of the second computing device, the data packet.
|