| CPC H04L 9/3263 (2013.01) [H04L 63/0428 (2013.01); H04L 63/1416 (2013.01)] | 18 Claims |
|
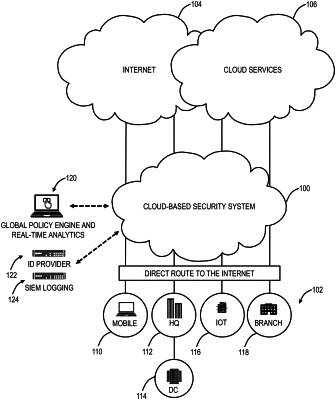
1. A method implemented as a node configured as any of a proxy, a Secure Web Gateway, and a Secure Internet Gateway, the method comprising steps of:
establishing a connection with a user device having a user associated with a tenant;
obtaining policy for the user;
monitoring traffic between the user device and the Internet including snooping session keys for any encrypted traffic;
analyzing the traffic based on the policy including utilizing the session keys on the encrypted traffic to decrypt the traffic for inspection thereof, wherein the analyzing is performed at a middle location of the connection with encrypted traffic and the analyzing includes checking for malicious traffic and Data Loss Prevention (DLP) for the tenant; and
one of allowing, blocking, or limiting the traffic based on the analyzing.
|