| CPC H04L 9/3242 (2013.01) [H04L 9/085 (2013.01); H04L 9/0894 (2013.01); H04L 9/3247 (2013.01); H04L 69/22 (2013.01)] | 20 Claims |
|
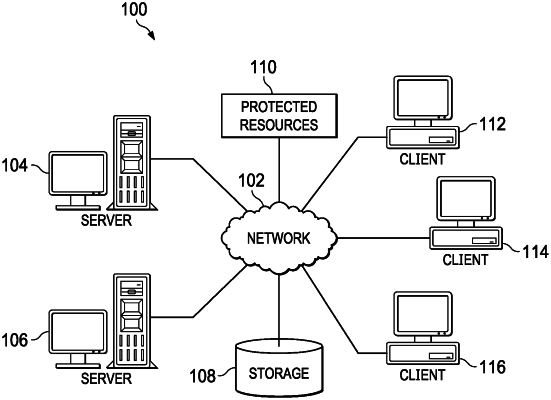
1. A computer-implemented method for resource user authentication and authorization, the computer-implemented method comprising:
generating, by a computer, an authentication code based on using a retrieved attribute-based encryption user key as a secret key for a keyed-hash message authentication code digital signature over a set of header fields of a protected resource access request received from a client device of a resource user via a network;
comparing, by the computer, the generated authentication code with an authentication code read within an embedded header field of the protected resource access request;
determining, by the computer, whether a match exists between the generated authentication code and the authentication code read within the embedded header field;
responsive to the computer determining that a match does exist between the generated authentication code and the authentication code read within the embedded header field, authenticating, by the computer, the resource user; and
performing, by the computer, decryption of an encrypted protected resource corresponding to the protected resource access request using the retrieved attribute-based encryption user key corresponding to the resource user in response to authentication of the resource user.
|