| CPC H04L 9/3239 (2013.01) [H04L 9/0643 (2013.01); H04L 9/0825 (2013.01); H04L 9/30 (2013.01); H04L 9/50 (2022.05)] | 17 Claims |
|
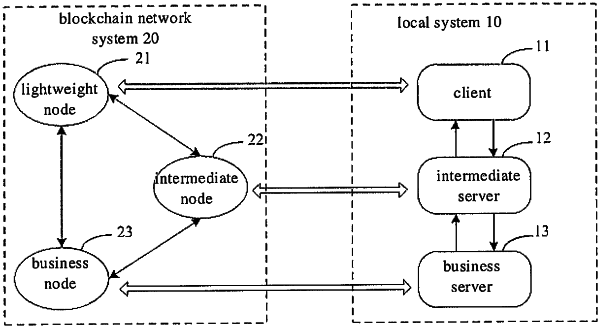
1. A private data processing method, executable by a client, comprising:
according to first operation behavior and associated data when initiating a user request, generating a first operation transaction request through a blockchain deployment protocol deployed in a blockchain node, and transmitting the first operation transaction request to a blockchain network for on-chain storage, wherein the first operation behavior and associated data is configured to verify rationality of the user request;
initiating the user request to an intermediate server according to an input of a user to request the intermediate server to perform intermediate business processing according to the user request and to initiate a target business processing request to a business server, wherein when performing the intermediate business processing, the intermediate server generates a second operation transaction request through a blockchain deployment protocol deployed in a blockchain node according to second operation behavior and associated data, and transmits the second operation transaction request to a blockchain network for on-chain storage, wherein the second operation behavior and associated data is configured to monitor abnormal operations of the intermediate server;
obtaining business result data fed back by the business server based on the target business processing request from the intermediate server, wherein the business result data is encrypted by using an account key of the user; and
decrypting the business result data by using the account key.
|