| CPC G06F 21/6245 (2013.01) [G06F 21/44 (2013.01); G06F 21/54 (2013.01); G06F 21/6218 (2013.01); G06F 21/78 (2013.01); G06F 21/53 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
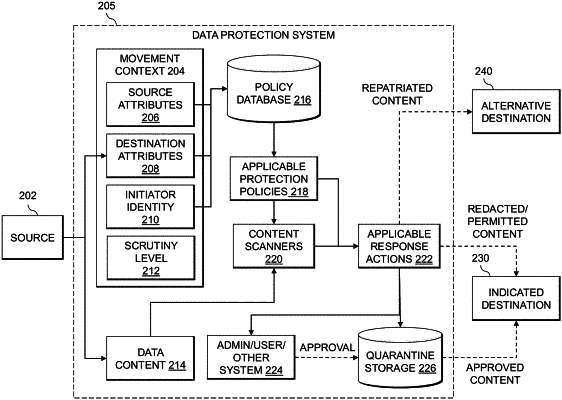
identifying a context of a data movement operation based at least in part on a source and an indicated destination of data associated with the data movement operation;
applying one or more data protection policies to the data movement operation based at least in part on the identified context, wherein a given data protection policy comprises one or more indications of one or more content scanners that are configured to detect data belonging to one or more regulated data classes;
selecting and executing at least a portion of the one or more content scanners based at least in part on a scrutiny level computed for the data movement operation; and
in response to detecting data associated with the data movement operation that belongs to at least one of the regulated data classes, performing one or more automated remedial actions associated with the at least one regulated data class;
wherein the method is performed by at least one processing device comprising a processor coupled to a memory.
|