| CPC G06F 21/6245 (2013.01) [G06F 21/602 (2013.01); G06F 21/604 (2013.01)] | 20 Claims |
|
1. A method of protecting information stored by an onboard computing system of a vehicle, the method comprising:
detecting a connection between a first user device of a first user and the onboard computing system;
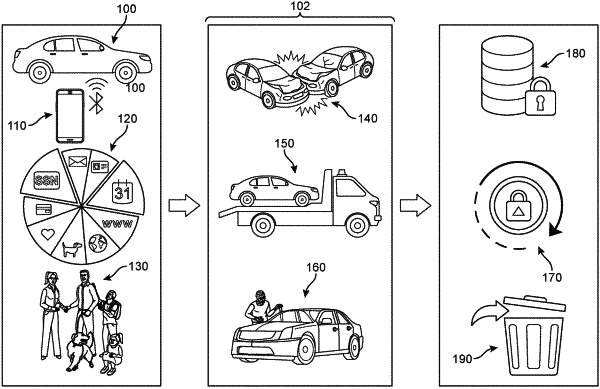
receiving, at the onboard computing system and from the first user device, a first set of data comprising personally identifiable information of the first user;
storing the first set of data in a memory of the onboard computing system;
receiving, by the onboard computing system, at least one configuration remote command from the first user device to remotely set at least one operational preference of the onboard computing system;
wherein the onboard computing system manages the first set of data using the at least one operational preference;
determining a triggering event has occurred after storing the first set of data
by detecting a change in ownership of the vehicle and receipt of a locking remote command from the first user using the first user device, the locking remote command being a remote command to lock down access of the onboard computing system to the first set of data;
executing, at the onboard computing system and in response to determining that the triggering event has occurred, a protective response directed to the first set of data;
wherein the protective response comprises locking down access of the onboard computing system to the first set of data while maintaining the first set of data in a storage of the onboard computing system;
receiving an unlocking remote command from the first user using the first user device, the unlocking remote command being a remote command to unlock access of the onboard computing system to the first set of data; and
restoring access of the onboard computing system to the first set of data after receiving the unlocking remote command.
|