| CPC G06F 21/6218 (2013.01) [G06F 21/602 (2013.01); G06F 2221/2107 (2013.01); G06F 2221/2141 (2013.01)] | 5 Claims |
|
1. A method for storing and reading data on a storage facility in an untrusted environment,
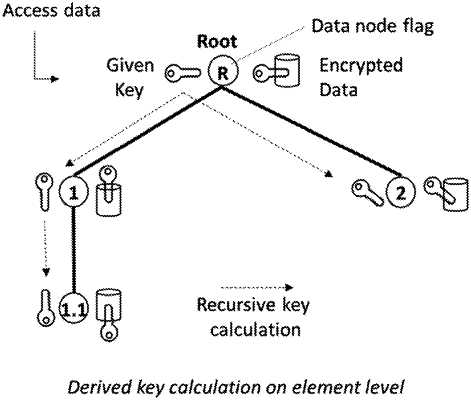
wherein the data is assigned to data nodes on a tree structure, each data node having (i) a data node flag that clearly identifies the data node in relation to one or more sibling data nodes, and (ii) one current data node key, and
wherein the tree structure includes a root data node for which at least one data node key is manually specified, and all child data nodes recursively calculate their current data node keys based on the root data node including a current parent data node key,
wherein the data is encrypted before being stored on the storage facility with the current data node key of the data node associated with the data and the data is encrypted after being read on the storage facility with the current data node key, the method comprising:
defining a data node key generation step that can be applied to each data node any number of times, time-independently, wherein applying the data node key generation step to a data node comprises:
generating a new data node key index for the data node,
calculating an additional data node key and setting the additional data node key as the current data node key by matching a result of a secure hash function applied at least to a data node marker of the data node, the new data node key index, and the current data node key of a parent data node,
creating or extending a volatile data node key list containing a data node key index column and a data node key column with an insertion of the new data node key index and the previously calculated additional data node key at an end of the volatile data node key list, the previously calculated additional data node key becoming the current data node key, and
creating or extending a non-volatile data node key parameter list containing a data node index column and a parent data node index column, with an insertion of the new data node key index of the data node into the data node index column and a last data node key index from a non-volatile data node key parameter list of the parent data node into the parent data node index column at an end of the non-volatile data node key parameter list so that only public indices are permanently saved; and
before data of the data node are saved:
identifying a path in the tree structure from the root data node to the data node,
tracking the identified path from a first child data node of the root data node to an additional data node,
comparing a last entry in the non-volatile data node key parameter list of the data node to a last entry in the non-volatile data node key parameter list of the parent data node of the data node, and
in response to determining that a last entry from the parent data node index column of the data node is not identical with a last entry in the data node index column from the non-volatile data node key parameter list of the parent data node of the data node:
applying the data node key generation step to the data node and each successor data node on the identified path,
encrypting particular data of the data node and each successor data node using the current data node key of the data node associated with the particular data, and
storing the non-volatile data node key parameter list assigned to the data node.
|