| CPC G06F 21/577 (2013.01) [G06F 8/65 (2013.01); G06F 21/552 (2013.01); G06F 21/554 (2013.01); G06F 21/566 (2013.01); G06F 21/602 (2013.01); H04L 9/0869 (2013.01); G06F 2221/0751 (2013.01)] | 19 Claims |
|
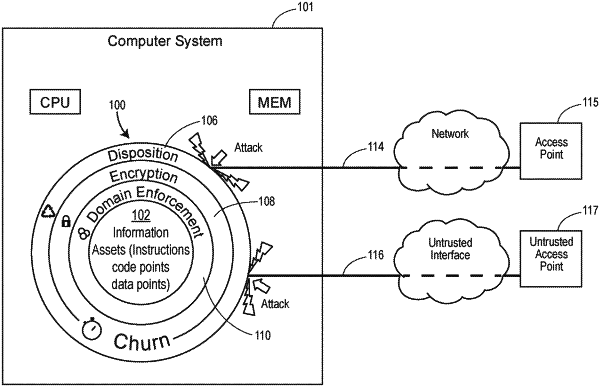
1. A computer-implemented method of securing a computer system against unauthorized access from an unauthorized agent, the method comprising:
assigning one or more attack information assets, stored in the computer system and targetable by an unauthorized agent to exploit a vulnerability of the computer system, as corresponding to one or more information domains including at least one of a code domain, a code pointer domain, a data object domain, a data object pointer domain, a relative distance between data objects domain, or an operation timing domain; and
for each information domain to which attack information assets were assigned, protecting the one or more attack information assets assigned to the information domain using one or more composable moving target defense layers of protection each having a respective churn cycle and a corresponding respective churn rate, wherein protecting the attack information assets includes reconfiguring each respective churn cycle at the corresponding respective churn rate.
|