| CPC G06F 21/577 (2013.01) [G06F 9/45558 (2013.01); G06F 2009/45579 (2013.01); G06F 2221/033 (2013.01)] | 15 Claims |
|
1. A non-transitory tangible computer readable storage medium having stored thereon a computer program for implementing a method of unifying software library access and prioritizing software library-based vulnerabilities for correction, the computer program including a set of instructions which, when executed by a computer, cause the computer to perform the steps of:
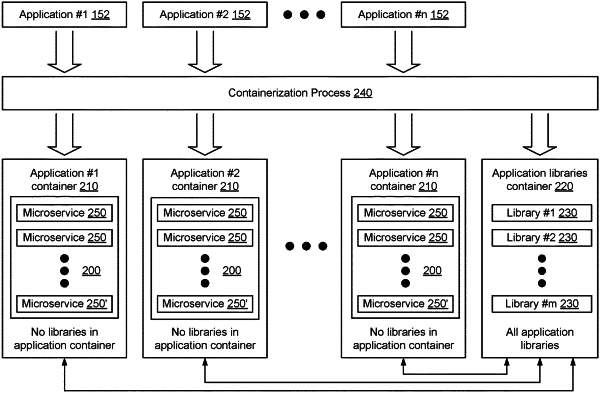
creating a shared library container by a containerization process, the shared library container containing a set of libraries but not executable application code;
creating a set of application containers by the containerization process, wherein each application container is an independent container, separate from the shared library container, and contains one or more applications implemented as executable application code for execution on an operating system of a storage system and configuration files, but not any library of the set of libraries that are contained in the shared library container, wherein at least some of the executable application code contained in the set of application containers reference one or more of the libraries contained in the shared library container;
determining severity values of known vulnerabilities associated with each of the libraries in the shared library container;
for each library in the shared library container, determining a percentage of the applications that use the library and a frequency with which the applications use the library; and
replacing one of the libraries in the shared library container to correct a vulnerability identified in the one of the libraries, without modifying the application code in any of the application containers.
|