| CPC G06F 16/2365 (2019.01) [G06F 21/552 (2013.01); G06F 21/6227 (2013.01); G06F 21/51 (2013.01); G06F 21/572 (2013.01)] | 20 Claims |
|
1. A method comprising:
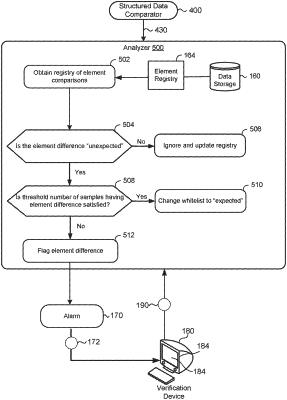
receiving, at data processing hardware, an indication of a possible instance of malicious activity for an element of structured data, the indication indicating that an activity of the element of structured data deviates from an assessment standard comprising attributes corresponding to the structured data;
identifying, by the data processing hardware, that the possible instance of malicious activity for the element of structured data differs from the assessment standard by more than a difference threshold;
in response to identifying that the possible instance of malicious activity for the element of structured data differs from the assessment standard by more than the difference threshold, identifying, by the data processing hardware, a plurality of other instances of activity for the element of structured data that deviated from the assessment standard, the plurality of other instances of activity stored in a registry in communication with the data processing hardware;
determining, by the data processing hardware, whether the possible instance of malicious activity for the element of structured data matches other instances of activity for the element of structured data that deviated from the assessment standard; and
when the possible instance of malicious activity for the element of structured data fails to match other instances of activity for the element of structured data, communicating, by the data processing hardware, the possible instance of malicious activity for the element of structured data as a security finding to an entity overseeing the structured data.
|