| CPC G06F 11/1405 (2013.01) [G06F 8/60 (2013.01); G06F 9/4881 (2013.01); G06F 9/541 (2013.01); G06F 11/1415 (2013.01); G06F 11/1482 (2013.01); G06F 11/3664 (2013.01); G06F 11/3692 (2013.01); G06F 21/51 (2013.01); G06F 21/54 (2013.01)] | 17 Claims |
|
1. A method, comprising:
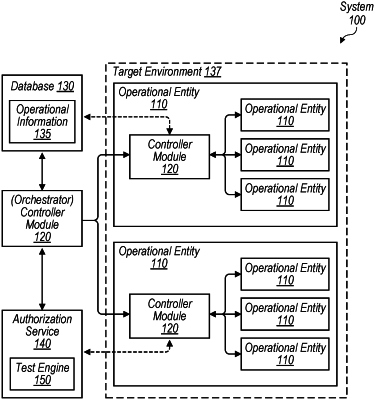
implementing, by a computer system, an authorization service that has a store of a plurality of security rules defining permissible actions that can be performed when implementing an operational scenario involving one or more operational entities included in a target computing environment, wherein the authorization service is accessible to a hierarchy of controller modules;
executing, by the computer system, at least a portion of the hierarchy of controller modules to implement the operational scenario, wherein the portion includes:
an orchestrator controller module at a top level of the hierarchy that is executable to issue one or more commands to one or more controller modules at one or more lower levels of the hierarchy in response to the authorization service confirming that the orchestrator controller module is authorized to issue the one or more commands; and
a particular controller module of the one or more controller modules, wherein the particular controller module is executable to:
access and locally store a subset of the plurality of security rules from the authorization service that is associated with the particular controller module, wherein the subset of security rules is validated periodically;
after receiving a first command of the one or more commands, verify that an action defined by the first command is permitted to be performed by the particular controller module under the subset of security rules; and
in response to determining that the action is permitted based on the verification, perform the action with respect to an operational entity managed by the particular controller module.
|