| CPC G06F 9/5072 (2013.01) [G06F 9/505 (2013.01); G06F 9/5077 (2013.01); G06F 9/547 (2013.01); G06F 11/3664 (2013.01)] | 17 Claims |
|
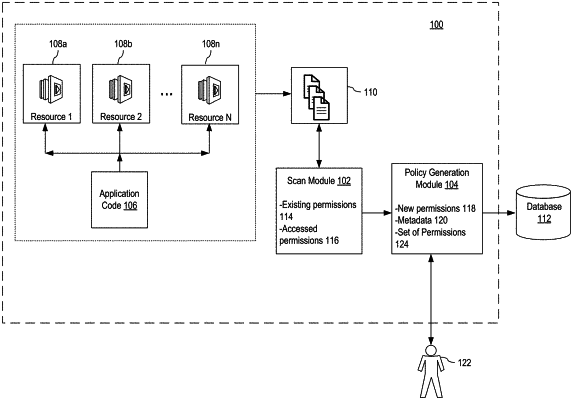
1. A computer implemented method for access management for applications, the method comprising:
(a) initializing, by one or more computing devices and at execution time of an application code, a scan of actions performed by the application code on resources of a cloud computing environment;
(b) identifying, by the one or more computing devices, an existing set of permissions for the resources;
(c) identifying, by the one or more computing devices, one or more accessed permissions by the application code based on the actions performed by the application code on the resources;
(d) generating, by the one or more computing devices, a new set of permissions for accessing the resources based on the identifying in (b) and (c), wherein the generating is performed by:
comparing the one or more accessed permissions by the application code identified in (c) to the existing set of permissions for the resources,
determining a difference between the one or more accessed permissions by the application code and the existing set of permissions, and
modifying the existing set of permissions to add or delete permissions to the existing set of permissions based on the one or more accessed permissions by the application code, wherein the modification results in the new set of permissions;
(e) transmitting, by the one or more computing devices, the new set of permissions to a database for storage and later retrieval; and
(f) applying, by the one or more computing devices, the new set of permissions to the resources when the application code is executed in a production environment.
|