| CPC G06F 9/45558 (2013.01) [G06F 9/5077 (2013.01); H04L 63/1441 (2013.01); H04L 67/568 (2022.05); G06F 2009/45587 (2013.01)] | 20 Claims |
|
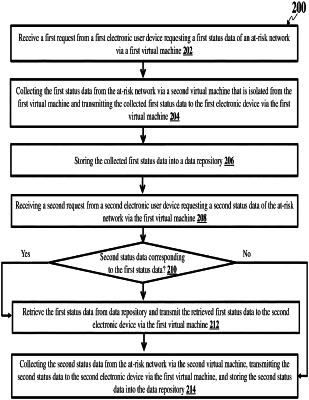
1. A computer-implemented method comprising:
receiving from an at-risk network, by a server, status data for the at-risk network via a collection virtual machine hosted by a hypervisor of the server;
caching, by the server, the status data for the at-risk network into a data repository accessible to a plurality of client virtual machines hosted by the hypervisor of the server, wherein the collection virtual machine is isolated from the plurality of client virtual machines; and
transmitting, by the server, the status data for the at-risk network to a client device via a client virtual machine of the plurality of client virtual machines, the server transmitting the status data via an inter-domain communication channel hosted by the hypervisor of the server.
|