| CPC H04L 63/20 (2013.01) | 20 Claims |
|
1. A method comprising:
causing the display of a UI enabling a user to indicate a cybersecurity search specification;
receiving user input comprising an indication of the cybersecurity search specification;
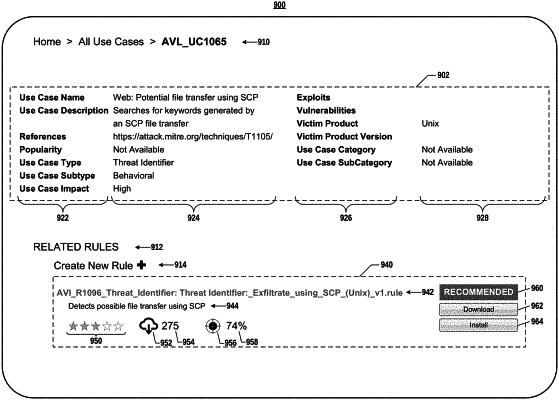
searching a security knowledge graph for SIEM-executable rules for processing the cybersecurity search specification, the security knowledge graph comprising a rule layer, an enterprise behavior layer, and a tactics/techniques/procedures (TTP) framework layer;
identifying a first set of one or more SIEM-executable rules corresponding to the cybersecurity search specification, from a plurality of SIEM-executable rules concerning multiple, separate enterprises, responsive to searching the security knowledge graph;
identifying a second set of one or more STEM-executable rules, responsive to searching the security knowledge graph, the second set of rules being associated with security concepts within a specific threshold degree of logical proximity to the first set of rules based on positions of corresponding nodes in the security knowledge graph;
causing the display of a UI indicating at least one rule of the first identified set of rules and at least one rule of the second identified set of rules, the UI enabling the user to indicate an implementation option for displayed rules;
receiving second user input comprising an indication of an implementation option;
causing the performance of processing based at least in part on the indication of the implementation option.
|