| CPC H04L 63/1433 (2013.01) [G06N 20/20 (2019.01); H04L 63/1441 (2013.01); H04L 63/20 (2013.01)] | 16 Claims |
|
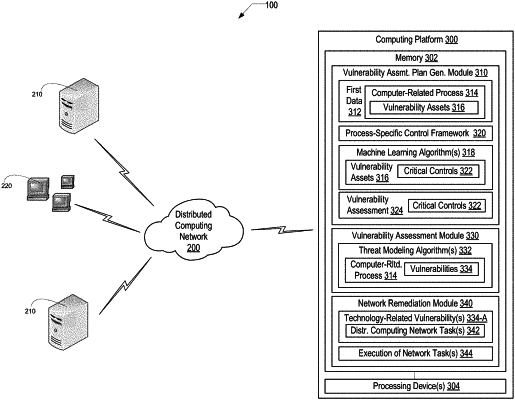
1. A system for defining security vulnerabilities of computer-related processes and implementing automated remediation, the system comprising:
a distributed computing network comprising a plurality of computing apparatus that are configured to communicate via the distributed computing network;
a computing platform disposed in one or more of the computing apparatus and comprising a memory and one or more processing devices in communication with the memory;
a vulnerability assessment plan generation module stored in the memory, executable by one or more of the processing devices and configured to:
receive first data from a plurality of disparate data sources;
identify, from the first data, critical vulnerability assets associated with a selected one of a plurality of computer-related processes;
identify one or more controls for a selected one of the computer-related processes based at least on the critical vulnerability assets; and
generate a vulnerability assessment specific to the selected computer-related process including the one or more controls;
a vulnerability assessment module stored in the memory, executable by one or more of the processing devices and configured to:
implement one or more threat modeling algorithms to define vulnerabilities for the selected one of the computer-related processes;
a network remediation module stored in the memory executable by one or more of the processing devices and configured to:
determine one or more network tasks for optimizing the distributed computing network-based on the defined vulnerabilities; and
in response to determining the one or more network tasks, execute at least one of the tasks to optimize the distributed computing network; and
a taxonomy module stored in the memory, executable by the one or more processing devices and configured to:
identify a plurality of computer-related critical functions;
receive second data from a plurality of second disparate data sources,
identify, from the second data, a plurality of computer-related critical services and a plurality computer-related processes; and
map (i) the identified computer-related critical functions to the computer-related critical services, (ii) the computer-related critical services to the computer-related processes and (iii) the computer-related processes to at least one of (a) one or more sub-processes associated with a computer-related process, (b) one or more entities responsible for a computer-related process, (c) one or more process flows for conducting a computer-related process, and (d) technology components required for a computer-related process.
|