| CPC H04L 63/1433 (2013.01) [H04L 61/4511 (2022.05); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/20 (2013.01)] | 18 Claims |
|
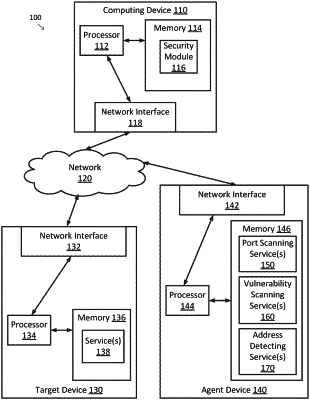
1. A computer-implemented method for analyzing network vulnerabilities, the method comprising:
determining an address for each target device included in a plurality of target devices, wherein determining the address for each target device comprises using one or more address detecting services, each of the one or more address detecting services using at least one of domain name service (DNS) information, autonomous system number (ASN) information, certificate information, or tracking information from opted-in end users;
for each target device included in the plurality of target devices:
pushing a port scanning task onto a primary port scanning queue or a secondary port scanning queue based on whether a number of failed, slow, incomplete, or anomalous port scans associated with the target device exceeds a threshold value, wherein a scanning frequency associated with the primary port scanning queue is greater than a scanning frequency associated with the secondary port scanning queue, the port scanning task being associated with the target device via the address of the target device, and
assigning the port scanning task from the primary port scanning queue or the secondary port scanning queue to a port scanning service;
for each port scanning task, receiving a port scanning result from the port scanning service assigned to the port scanning task, the port scanning result including a list of one or more open ports for the target device associated with the port scanning task;
for each open port included in each port scanning result, assigning a vulnerability scanning task to an associated vulnerability scanning service;
receiving a vulnerability scanning result for each vulnerability scanning task; and
generating a report based on at least one of the port scanning results or the vulnerability scanning results.
|