| US 11,736,498 B1 | ||
| Stateful detection of cyberattacks | ||
| Wen-Kwang Tsao, Taipei (TW); Mun-Hou Wong, Taipei (TW); Annie Bu, Taipei (TW); Chia-Yen Chang, Taipei (TW); Jonathan James Oliver, Melbourne (AU); Liam Huang, Taipei (TW); Allen Lai, Taipei (TW); Chien-Yi Chiu, Taipei (TW); and Ping-Huan Wu, Taipei (TW) | ||
| Assigned to Trend Micro Incorporated, Tokyo (JP) | ||
| Filed by Trend Micro Incorporated, Tokyo (JP) | ||
| Filed on Jan. 28, 2020, as Appl. No. 16/774,358. | ||
| Claims priority of provisional application 62/893,354, filed on Aug. 29, 2019. | ||
| Int. Cl. H04L 29/06 (2006.01); H04L 9/40 (2022.01); G06N 5/04 (2023.01); G06F 16/2458 (2019.01); G06F 16/242 (2019.01) | ||
| CPC H04L 63/1416 (2013.01) [G06F 16/2425 (2019.01); G06F 16/2471 (2019.01); G06N 5/04 (2013.01)] | 20 Claims |
|
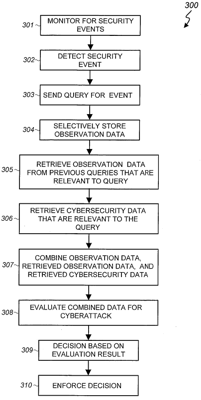
1. A method of detecting cyberattacks, the method comprising:
detecting a security event; in response to detecting the security event, generating a query that includes observation data of the security event; searching a first database for other observation data that are relevant to the observation data, the other observation data being of other security events and included in previous other queries that were generated in response to detecting the other security events, the other observation data being stored in the first database; generating a set of observation data that comprises the observation data and the other observation data; searching a second database for cybersecurity data that are relevant to the observation data; generating a combined input vector that indicates presence of corresponding features in the set of observation data and the cybersecurity data; and inputting the combined input vector into a detector to generate a decision that is responsive to the query, the decision being based on evaluation of the combined input vector by the detector to determine whether the security event is a cyberattack. |