| US 11,736,497 B1 | ||
| Cyber security platform and method | ||
| Albert Rooyakkers, Sunnyvale, CA (US); Samuel Galpin, Nashua, NH (US); and Christopher Harlow, Millis, MA (US) | ||
| Assigned to Bedrock Automation Platforms Inc., San Jose, CA (US) | ||
| Filed by Bedrock Automation Platforms Inc., San Jose, CA (US) | ||
| Filed on Mar. 19, 2019, as Appl. No. 16/358,161. | ||
| Claims priority of provisional application 62/644,827, filed on Mar. 19, 2018. | ||
| Int. Cl. H04L 29/06 (2006.01); H04L 9/40 (2022.01); G05B 19/418 (2006.01) | ||
| CPC H04L 63/1416 (2013.01) [G05B 19/4185 (2013.01); H04L 63/06 (2013.01); H04L 63/0823 (2013.01); H04L 63/20 (2013.01); G05B 2219/23317 (2013.01); G05B 2219/24159 (2013.01)] | 18 Claims |
|
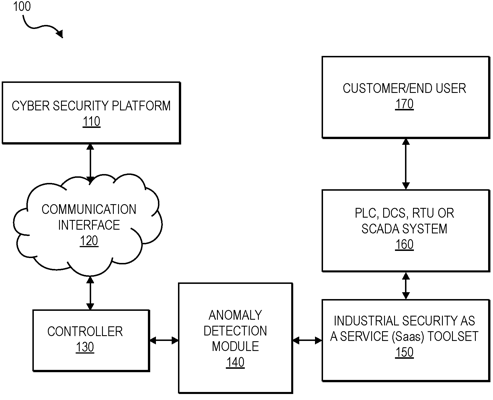
1. An industrial control system comprising:
a controller configured to operatively couple to at least a sensor and an actuator device on a network, the controller including one or more computer processors and one or more computer-readable storage media; and a cyber security platform for detecting network intrusions and/or anomalous behavior on the industrial control system, the cyber security platform comprising program instructions stored on the one or more computer-readable storage media for execution by at least the one or more processors, the program instructions including: program instructions to keep out unauthorized users from changing a mode of the controller based on a virtual key lock; responsive to detecting a second controller or a communication point attempting to connect to the network, program instructions to record at least one of: an Internet Protocol version 4 (IPv4)/Internet Protocol version 6 (IPv6) address of an initiating host, a Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) port number, a subject name in a certificate provided by the initiating host, a certificate thumbprint, or a status indicating a success or failure to connect to the network; responsive to detecting open port scanning activity on the network, program instructions to record information associated with the open port scanning activity including a source Internet Protocol (IP) address, a destination port, a network protocol (TCP or UDP), or incoming packet rates; responsive to detecting a system time change, program instructions to record an IP address that initiated the system time change and at least one of: a time change or a current system time; and responsive to detecting either the second controller or a communication point attempting to connect to the network, open port scanning activity on the network, or a system time change, program instructions to initiate an alert on an alert device connected to the controller, wherein the alert indicates an intrusion is detected. |