| CPC H04L 63/0815 (2013.01) [H04L 63/0853 (2013.01); H04L 63/108 (2013.01)] | 20 Claims |
|
1. A computer-implemented method comprising:
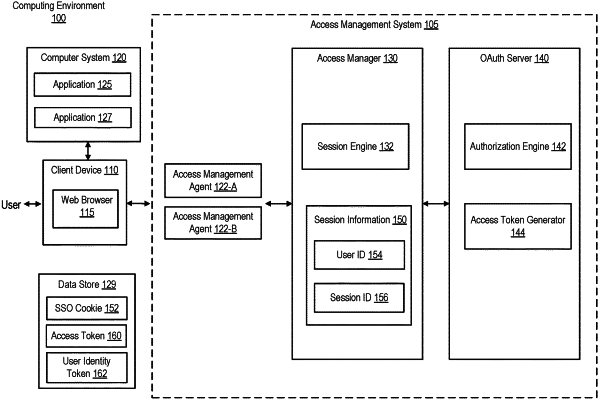
receiving, by an application, from an access management system, a user identity token, the user identity token including information identifying a user and a session identifier associated with a Single Sign-On (SSO) session;
storing, by the application, the user identity token;
sending, by the application, to the access management system, an access token request, the access token request including the session identifier associated with the SSO session, wherein the access management system retrieves session information associated with the SSO session based on the session identifier, and determines that the SSO session is valid based on the session information, wherein the access management system determines the SSO session is valid by determining a session expiration time based on the session information, by determining that the session expiration time has not yet been reached, by determining a timeout duration based on the session information, and by determining that the SSO session has not timed out based upon the timeout duration;
receiving, by the application, from the access management system, if the SSO session is valid, an access token that enables the application to access to a protected resource, the access token being different from the user identity token; and
using, by the application, the access token to access the protected resource.
|