| CPC G07C 9/22 (2020.01) [G06N 20/00 (2019.01); G07C 9/28 (2020.01); H04L 63/0272 (2013.01); H04W 12/63 (2021.01); H04W 12/64 (2021.01)] | 20 Claims |
|
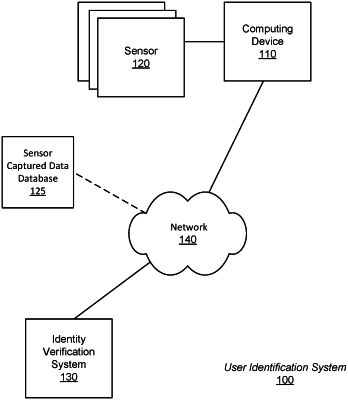
1. A non-transitory computer-readable medium comprising stored computer-readable instructions that, when executed by one or more processors, cause the one or more processors to:
identify a target user requesting access to an operational context assigned an operational security threshold at a particular time, wherein the target user performs an action to request access;
access a machine-learned model trained based on training data representing the action of performed by the target user;
input data representing the action to the machine-learned model to generate an identity confidence value describing a probability that the action was performed by the target user;
determine a decayed identity confidence value by applying a set of decay parameters to the identity confidence value, wherein the set of decay parameters are determined based on the operational context and the decayed identity confidence value represents a confidence in an identity of the target user at the particular time; and
grant the target user access to the operational context responsive to determining the decayed identity confidence value to be greater than the operational security threshold.
|