| CPC G06F 21/577 (2013.01) [G06F 8/71 (2013.01); G06F 11/3664 (2013.01); G06F 11/3684 (2013.01); G06F 2221/033 (2013.01)] | 20 Claims |
|
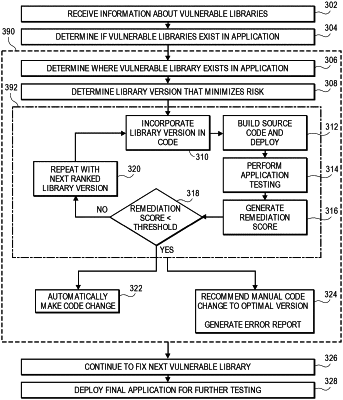
1. A method comprising:
receiving, by a remediation computer, a candidate application that uses a plurality of code libraries;
identifying, by the remediation computer, a vulnerable library from the plurality of code libraries;
obtaining, by the remediation computer, a list of a plurality of versions of the vulnerable library;
for each of the plurality of versions of the vulnerable library in the list:
identifying one or more risks, wherein each of the identified one or more risks is assigned a risk score;
assigning an intermediate risk score to each of the identified one or more risks based on the risk score for each of the identified one or more risks;
evaluating one or more operational risks to generate a change score;
sorting, by the remediation computer, the plurality of versions of the vulnerable library in the list based on the generated change score;
determining a version of the vulnerable library that minimizes risk from the sorted list; and
incorporating the determined version of the vulnerable library that minimizes the risk into the candidate application.
|