| CPC G06F 21/53 (2013.01) [G06F 12/1408 (2013.01); G06F 12/1466 (2013.01); G06F 21/602 (2013.01); G06F 21/606 (2013.01); G06F 21/72 (2013.01)] | 21 Claims |
|
1. A method comprising:
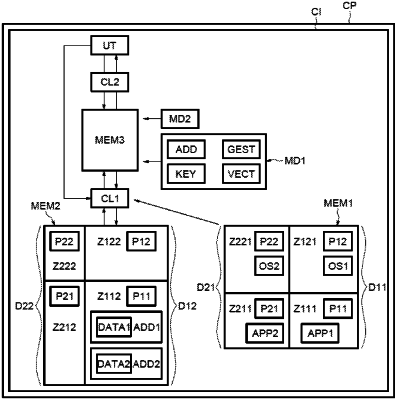
storing at least one first software application containing encrypted instructions in a first secured memory zone of a first memory, the first secured memory zone having a first level of access rights;
storing a first item of operating software for a processor in a second secured memory zone of the first memory, the second secured memory zone having a second level of access rights that is higher than the first level of access rights;
storing at least one second software application in a first unsecured memory zone of the first memory, the first unsecured memory zone having a third level of access rights;
storing a second item of operating software for the processor in a second unsecured memory zone of the first memory, the second unsecured memory zone having a fourth level of access rights that is higher than the third level of access rights;
verifying a first integrity of the at least one first software application;
decrypting the encrypted instructions that are considered to exhibit integrity;
executing, by the processor, the decrypted instructions to generate data;
encrypting the generated data; and
storing the encrypted data in a second memory zone having the first level of access rights, the second memory zone forming part of a second memory having a partition of domains and of memory zones that is identical to that of the first memory with respective levels of access rights that are homologous to those of the first memory, and the data generated by executing an item of software stored in one of the memory zones of the first memory being stored in a homologous memory zone of the second memory.
|