| CPC H04L 63/205 (2013.01) [G06F 16/252 (2019.01); G06F 21/577 (2013.01); G06N 3/04 (2013.01); G06N 5/04 (2013.01); H04L 63/1433 (2013.01); G06F 2221/034 (2013.01)] | 18 Claims |
|
1. A computer-implemented method, comprising:
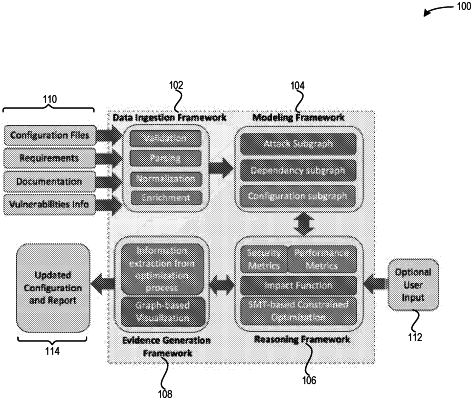
determining, by a computing device, information sources associated with hardware and software components of a system,
wherein the information sources include at least specification sheets, standard operating procedures, user manuals, and vulnerability databases;
selecting a set of categories of vulnerabilities in a vulnerability database;
ingesting the information sources to obtain data in a normalized format;
extracting, from the ingested information sources, configuration information, vulnerability information, dependency information, and functionality requirements to create a model for the system,
wherein the system comprises an Internet of Things (IoT) system which comprises a configuration graph, an attack graph, and a dependency graph, and
wherein the extracted configuration information is used to generate the configuration graph, the extracted vulnerability information is used to generate the vulnerability graph, and the extracted dependency information is used to generate the dependency graph; and
displaying, on a screen of a user device, one or more interactive elements which allow the user to view or select the information sources and the categories of vulnerabilities, initiate ingesting the information sources, and view the extracted configuration information.
|