| CPC H04L 63/1491 (2013.01) [G06F 9/547 (2013.01); H04L 63/1416 (2013.01); H04L 67/133 (2022.05)] | 18 Claims |
|
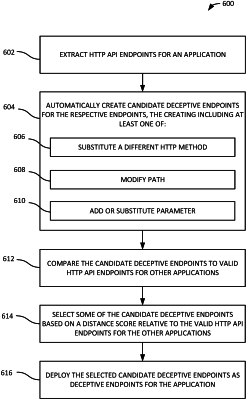
16. One or more non-transitory computer-readable storage media storing computer-executable instructions for securing an application, the securing comprising:
extracting a plurality of valid hypertext transfer protocol (HTTP) application programing interface (API) endpoints for an application, the valid endpoints having an HTTP method and a path;
automatically creating candidate deceptive endpoints for respective of the valid endpoints, the creating comprising one or more of:
substituting a different HTTP method for the HTTP method of the valid endpoint;
modifying the path of the valid endpoint; or
adding a new parameter or substituting the new parameter for an existing parameter of the valid endpoint;
comparing the candidate deceptive endpoints to valid HTTP API endpoints for other applications;
selecting some of the candidate deceptive endpoints based on a distance score relative to one or more of the valid HTTP API endpoints for the other applications; and
deploying the selected candidate deceptive endpoints as deceptive endpoints for the application, wherein a requesting computing device accessing one of the deceptive endpoints indicates a malicious action.
|