| CPC H04L 63/1433 (2013.01) [G06F 8/65 (2013.01)] | 20 Claims |
|
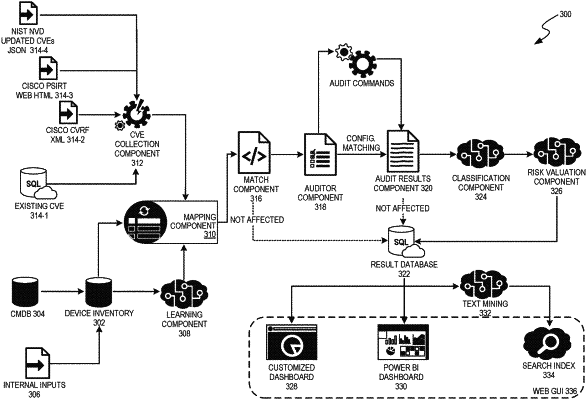
1. A method for adaptive vulnerability management of a computer system, the method comprising:
collecting vulnerability information over a network from a publishing source,
wherein the vulnerability information includes a known vulnerability of a first computer asset,
wherein the vulnerability information includes a set of cybersecurity vulnerabilities and exposures (CVEs) published on a public network,
at least some of the CVEs being in a human-readable format;
collecting system information of the computer system, the computer system being subject to the vulnerability management,
wherein the system information includes information about a second computer asset of the computer system; and
processing the collected vulnerability information and the collected system information by:
interpreting at least some of the human-readable CVEs with natural language processing (NLP) and correlating the interpreted CVEs with the collected system information;
identifying a potential vulnerability of the second computer asset based on a correlation between the interpreted CVEs and the collected system information;
storing, in a cloud-based results database, a subset of the collected vulnerability information,
wherein the subset of the collected vulnerability information does not match the collected system information; and
generating, based on text extracted from the subset of the collected vulnerability information stored in the cloud-based results database, a search index that is accessible from a web-based graphical user interface and enables access to processed analytics of the collected vulnerability information.
|