| CPC H04L 63/1433 (2013.01) [H04L 41/145 (2013.01); H04L 63/1416 (2013.01)] | 22 Claims |
|
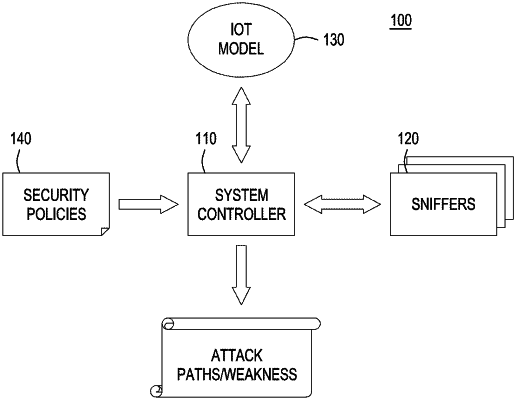
1. A method for determining a weakness or risk for devices of an Internet-of-things (IoT) network, comprising:
determining a representation of a physical environment of the IoT network and expected physical and cyber interactions between the devices of the IoT network based at least in part on operating characteristics of the devices of the IoT network;
monitoring the physical environment and actual interactions between the devices of the IoT network to generate a network model including at least one of uncharacteristic physical or cyber interaction paths between the devices of the IoT network over which physical or cyber interactions can potentially occur;
comparing the determined representation of the physical environment of the IoT network and the expected physical and cyber interactions between the devices of the IoT network and the network model to determine unexpected interaction paths between devices of the IoT network;
based on the determined unexpected interaction paths between the devices of the IoT network, determining at least one weakness or risk of at least one of the IoT network or of at least one of the devices of the IoT network; and
providing a metric of security of at least one of the IoT network or of at least one of the devices of the IoT network based on at least one of the determined weakness or risk.
|