| CPC H04L 63/1425 (2013.01) [G06F 21/552 (2013.01); H04L 43/062 (2013.01); H04L 43/16 (2013.01); H04L 63/1416 (2013.01); H04L 63/1441 (2013.01); H04L 63/1491 (2013.01); G06F 21/56 (2013.01); H04L 63/0263 (2013.01)] | 20 Claims |
|
1. A computer-implemented method performed by one or more processors, the method comprising:
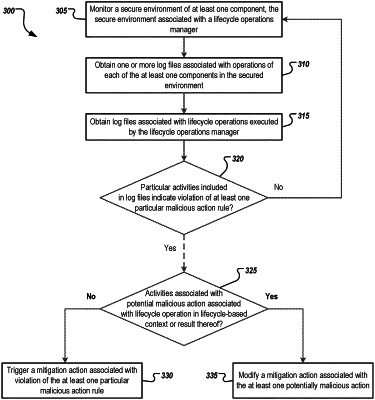
obtaining, by an intrusion detection system, one or more log files associated with operations of each of at least one component of a secured environment;
obtaining, by the intrusion detection system, log files associated with lifecycle operations executed by a lifecycle operations manager on at least one respective component of the at least one component in the secured environment;
accessing, by the intrusion detection system, a lifecycle-based context associated with the lifecycle operations manager, wherein the lifecycle-based context stores contextual information associated with the lifecycle operations;
pre-filtering, by the intrusion detection system and based on the contextual information stored in the lifecycle-based context, the log files to identify at least one potentially malicious action prior to determining whether a malicious action exists in the log files, wherein pre-filtering includes removing data from the log files that is not associated with entries in the lifecycle-based context;
determining, by the intrusion detection system and based on the pre-filtered log files, whether a violation of at least one particular malicious action rule from a malicious action rules set is associated with one or more lifecycle operations associated with the lifecycle-based context; and
in response to determining that the violation of the at least one particular malicious action rule is associated with the one or more of the lifecycle operations associated with the lifecycle-based context, triggering a mitigation action associated with the violation of the at least one particular malicious action rule.
|