| CPC H04L 63/0428 (2013.01) [H04L 9/0643 (2013.01); H04L 9/088 (2013.01); H04L 9/3215 (2013.01); H04L 9/3236 (2013.01); H04L 12/66 (2013.01); H04L 45/745 (2013.01); H04L 47/20 (2013.01); H04L 61/2592 (2013.01); H04L 61/5007 (2022.05); H04L 61/5038 (2022.05); H04L 2209/125 (2013.01)] | 18 Claims |
|
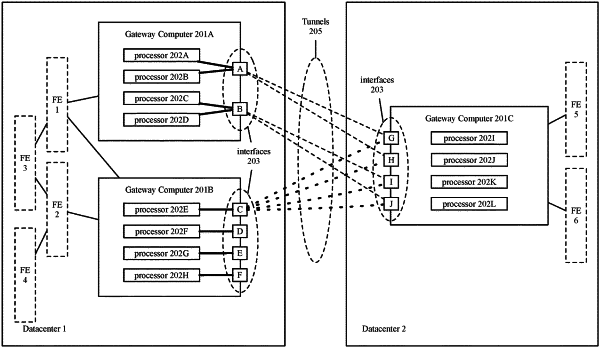
1. A method of configuring a first computing device to assign different processing units to use different encryption-secured tunnels to transmit data messages requiring encryption, the method comprising:
associating a virtual tunnel interface (VTI) to each of a plurality of encryption-secured tunnels between a set of interfaces of first and second computers, wherein each encryption-secured tunnel specifies an encryption policy, the encryption policy specifying a key value associated with the encryption-secured tunnel's associated VTI;
assigning a private network address to each VTI;
for each processing unit, (1) creating a rule for a desired encryption policy in a network address rule table that identifies a routing lookup table to use for data messages matching a network-address-based rule and (2) creating a custom routing lookup table that identifies the private network address of at least one VTI as a next hop for a data message matching the network-address-based rule that points to the custom routing lookup table,
wherein the network address rule table and the custom routing lookup table are used to select an encryption-based tunnel to transmit a data message requiring encryption.
|