| CPC H04L 63/0227 (2013.01) [H04L 9/0861 (2013.01); H04L 9/16 (2013.01); H04L 9/3273 (2013.01); H04L 47/19 (2013.01); H04L 47/24 (2013.01); H04L 63/0236 (2013.01); H04L 63/0876 (2013.01); H04L 63/1441 (2013.01); H04L 69/22 (2013.01); H04L 63/0272 (2013.01); H04L 63/145 (2013.01); H04L 63/164 (2013.01)] | 27 Claims |
|
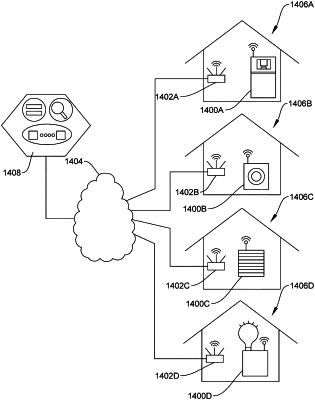
1. A product for securing communications of a plurality of networked computing devices, the product comprising a non-transitory computer-readable storage medium having computer-readable program code embodied therein, the computer-readable program code executable by a processor to perform communication management operations, the communication management operations comprising:
i) consuming a first network packet to obtain a first payload and a destination port number, the destination port number assigned to a destination port on one of the plurality of networked computing devices;
ii) confirming the first payload conforms to at least one of a data model pre-assigned to the destination port number;
iii) after confirmation that the first payload conforms to the data model for the destination port, forming a second network packet comprising a second payload, and at least one of a local program identification code, and a data model identification code; and
iv) executing at least one instruction to send the second network packet to network security software to the destination port on the one of the plurality of networked computing devices via a secure communication pathway.
|