| CPC H04L 49/357 (2013.01) [H04L 43/022 (2013.01); H04L 47/2483 (2013.01); H04L 63/101 (2013.01); H04L 63/1408 (2013.01)] | 20 Claims |
|
1. A computer-implemented method for handling soft zoning violations, the method comprising:
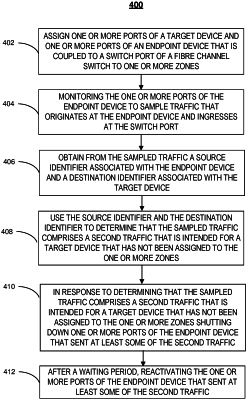
assigning a first target device and an endpoint device that is coupled to a switch port of a Fibre Channel (FC) switch to one or more zones in a soft zoning environment;
in response to the endpoint device logging into the FC switch, obtaining sampled traffic that originates at the endpoint device and ingresses at the switch port;
obtaining from the sampled traffic a source identifier associated with the endpoint device and a destination identifier associated with a target device; and
using the source identifier and the destination identifier to determine that the sampled traffic comprises a second traffic that is intended for a second target device that has not been assigned to the one or more zones, performing one or more actions to restrict the second traffic.
|