| CPC H04L 9/3242 (2013.01) [H04L 9/085 (2013.01); H04L 9/0869 (2013.01)] | 20 Claims |
|
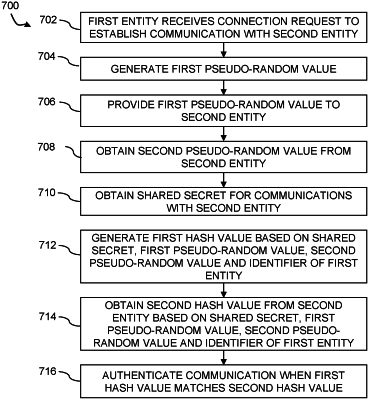
1. A method, comprising:
receiving, by a first entity associated with a communication between a first physical port of the first entity and a second physical port of a second entity, a connection request to establish a communication with the second entity;
generating, by the first entity, a first pseudo-random value based at least in part on a first time-based value;
providing, by the first entity, the first pseudo-random value to the second entity;
obtaining, by the first entity, a second pseudo-random value from the second entity, wherein the second pseudo-random value is based at least in part on a second time-based value, wherein at least one of the first time-based value and the second time- based value is obtained by applying a hash function to a respective value derived from at least a timestamp;
obtaining, by the first entity, a first shared secret established, prior to the receiving of the connection request, for communications with the second entity;
generating, by the first entity, a first hash value based at least in part on the first shared secret, the first pseudo-random value and the second pseudo-random value;
obtaining, by the first entity, a second hash value from the second entity based at least in part on the first shared secret, the first pseudo-random value and the second pseudo-random value;
authenticating, by the first entity, the communication in response to the first entity validating the first hash value using the second hash value; and
generating a new shared secret following the authenticating, wherein the second entity and at least one additional entity connect to the first entity using the new shared secret;
wherein the method is performed by at least one processing device of the first entity, said at least one processing device comprising a processor coupled to a memory.
|