| CPC H04L 9/008 (2013.01) [H04L 9/0869 (2013.01); H04L 2209/34 (2013.01)] | 1 Claim |
|
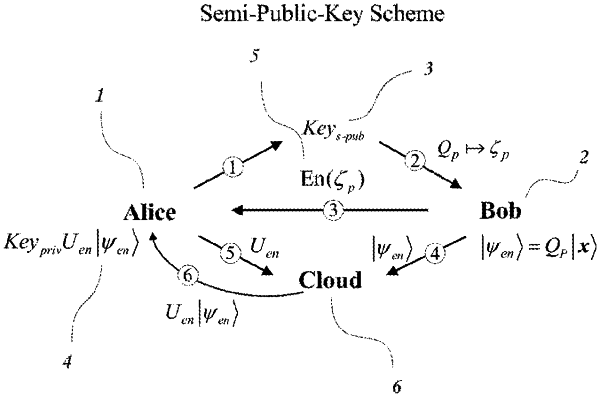
1. A method of constructing a semi-public key system in Quotient Algebra Partition (QAP)-based homomorphic encryption (HE), by an algebraic structure, QAP, and an arithmetic operation of homomorphic encryption, wherein the method comprises:
S1: encryption: comprising key generation and encoding;
S11: key generation: a data receiver generates a semi-public key, Keys-pub and a private key, Keypriv;
wherein the semi-public key Keys-pub, randomly generates an arbitrary k-qubit operation from a gigantic number of invertible gates of the same qubits;
the private key, Keypriv, for decryption is represented by Keypriv=
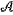 †P†, which is a product of two k-qubit operators, †P†, which is a product of two k-qubit operators, 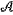 † and P†; wherein the semi-public key, Keys-pub is published in public space to transforming a plaintext to a ciphertext by anyone; and the private key, Keypriv, is retained by the data receiver to decrypt the encrypted ciphertext; † and P†; wherein the semi-public key, Keys-pub is published in public space to transforming a plaintext to a ciphertext by anyone; and the private key, Keypriv, is retained by the data receiver to decrypt the encrypted ciphertext;S12: encoding: a data provider provides a k-qubit plaintext, |x
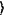 , a k-qubit operation Qp generated by the semi-public key, Keys-pub; an encoded state of ciphertext |ψen , a k-qubit operation Qp generated by the semi-public key, Keys-pub; an encoded state of ciphertext |ψen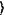 =Qp|x =Qp|x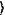 with the same qubit length is obtained; the semi-public key, Keys-pub, encodes a binary string ζp, which is 1-to-1 correspondence to Qp according to a given code system Gcrypt, into an encrypted message En(ζp) and sends it to the data receiver through a communication channel of small resource; and the data provider sends the ciphertext |ψen with the same qubit length is obtained; the semi-public key, Keys-pub, encodes a binary string ζp, which is 1-to-1 correspondence to Qp according to a given code system Gcrypt, into an encrypted message En(ζp) and sends it to the data receiver through a communication channel of small resource; and the data provider sends the ciphertext |ψen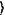 to a computation provider; to a computation provider;S2: Computation:
S21: a k-qubit arithmetic operation M is given to be operated and output a homomorphic encryption operation Uen enable to be conducted on the encrypted state |ψen
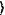 ; after receiving the encrypted message En(ζp) from the data provider and obtaining the corresponding k-qubit operation Qp by the decryption process in Gcrypt, the data receiver produces a computational instructions of the homomorphic encryption operation Uen with a form: ; after receiving the encrypted message En(ζp) from the data provider and obtaining the corresponding k-qubit operation Qp by the decryption process in Gcrypt, the data receiver produces a computational instructions of the homomorphic encryption operation Uen with a form: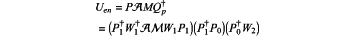 where QP†=W1W2 is a product of a qubit permutation W1 and an operation W2 comprising of elementary gates (CNOTs, SWAPs, Toffolis, CSWAPs), Pj=0,1 and P are qubit permutations following the nilpotent condition PW1P1=I2n, and then sends Uen to the computation provider;
S22: the computation provider receives the computational instructions to computes Uen|ψen
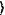 and an encrypted evaluation is obtained; and an encrypted evaluation is obtained;S3: Decryption:
the computation provider conducts homomorphic encryption computation Uen|ψen
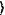 and sends the encrypted evaluation to the data receiver; the data receiver decrypts the evaluation by applying the private key Keypriv= and sends the encrypted evaluation to the data receiver; the data receiver decrypts the evaluation by applying the private key Keypriv=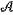 †P† to the state Uen|ψen †P† to the state Uen|ψen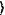 , which is written as , which is written as 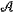 †P†Uen|ψen †P†Uen|ψen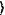 =M|x =M|x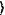 , and then obtains the unencoded result M|x , and then obtains the unencoded result M|x . . |