| CPC G06F 21/72 (2013.01) [G06F 21/85 (2013.01); G06F 21/602 (2013.01)] | 15 Claims |
|
1. A method of managing access to a security circuit implemented in a System on Chip, the System on Chip comprising:
at least two hardware masters;
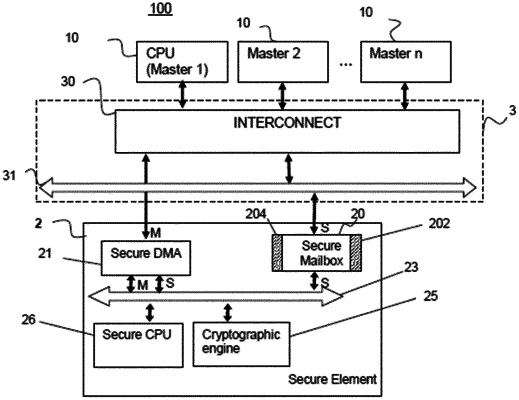
a security circuit for executing requests received from one or more hardware masters, wherein each request is a command for execution of a function corresponding to a cryptographic service by the security circuit;
a communication infrastructure for connecting said at least two hardware masters to the security circuit, the communication infrastructure being based on a given interface communication protocol;
the security circuit comprising a Secure Mailbox,
the requests received by the security circuit being executed by a secure processor,
the secure mailbox isolating the secure processor from the hardware masters so that the hardware masters and the secure processor cannot communicate directly,
wherein the method comprises:
receiving a request from one or more hardware masters at the security circuit through the communication infrastructure, each request received from a hardware master comprising at least one service identifier identifying a service;
filtering, by the Secure Mailbox, requests received from said hardware masters, said filtering step comprising determining at least one indicator bit, in response to the receipt of a request from a given hardware master, using at least a part of a master identifier identifying said hardware master, said indicator bit indicating whether said master is allowed access to the Security circuit, said master identifier being a hardware identifier received with the request through the communication protocol, said step of filtering the requests being based on the bit indicators determined for each request;
the method further comprising executing, by the security processor, the filtered requests.
|