| CPC G06F 21/6245 (2013.01) [G06F 16/211 (2019.01); G06F 16/215 (2019.01); G06F 16/24568 (2019.01); G06Q 10/067 (2013.01); H04L 63/1416 (2013.01); H04L 63/1425 (2013.01); H04L 63/1441 (2013.01)] | 20 Claims |
|
1. A computer program product comprising computer executable code embodied in a non-transitory computer readable medium that, when executing on one or more computing devices, performs the steps of:
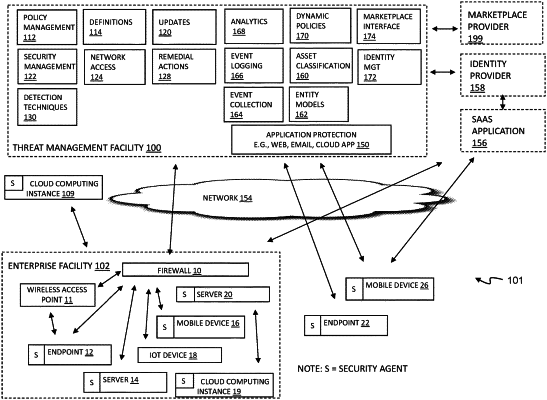
receiving an event stream including security events from an enterprise network at a stream service;
storing the event stream in a data lake;
storing a plurality of queries for execution against the event stream, the plurality of queries configured to investigate security issues within the enterprise network based on the event stream;
monitoring a usage of the plurality of queries at one or more administrative consoles to a threat management facility for the enterprise network;
identifying a usage history based on the usage of the plurality of queries, the usage history including a specific pattern of queries correlated to an identification of a threat; and
initiating a responsive remedial action to the threat by the threat management facility based on the usage history.
|