| CPC G06F 21/577 (2013.01) [G06F 8/433 (2013.01); G06F 8/71 (2013.01); G06F 8/77 (2013.01); G06F 2221/033 (2013.01)] | 19 Claims |
|
1. A system comprising:
a non-transitory memory; and
one or more hardware processors coupled to the non-transitory memory to execute instructions from the non-transitory memory to perform operations comprising:
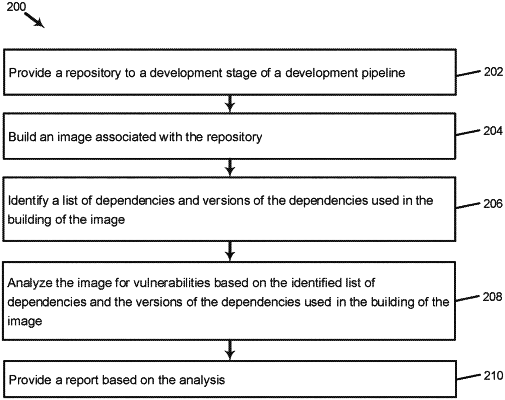
providing a repository to a development stage of a development pipeline;
building an image associated with the repository;
identifying a list of dependencies and versions of the dependencies used in the building of the image;
determining whether one or more portions of the image utilizes dependencies verified as free of a security vulnerability in a prior version of the image, wherein the security vulnerability corresponds to an aspect of the image which may be exploited;
responsive to identifying at least one portion of the image that utilizes a dependency verified as being free of the security vulnerability, skipping an analysis of the at least one portion of the image;
analyzing a remaining portion of the image for the security vulnerability based on the identified list of dependencies and the versions of the dependencies used in the building of the image;
determining whether one or more portions of the image utilizes dependencies unverified as free of the security vulnerability;
responsive to identifying at least one portion of the image that utilizes a dependency unverified as being free of the security vulnerability, retrieving a closest-match version of the dependency unverified as being free of the security vulnerability that has been verified as free of the security vulnerability; and
providing a report based on the analyzing.
|