| CPC G06F 21/54 (2013.01) [G06F 21/554 (2013.01); G06F 21/564 (2013.01); G06F 21/568 (2013.01)] | 20 Claims |
|
1. A computer-implemented method for detecting malware by linking transfer service activities to source programs, at least a portion of the method performed by a computing device comprising one or more processors, a memory, and an operating system stored within the memory, the computer-implemented method comprising:
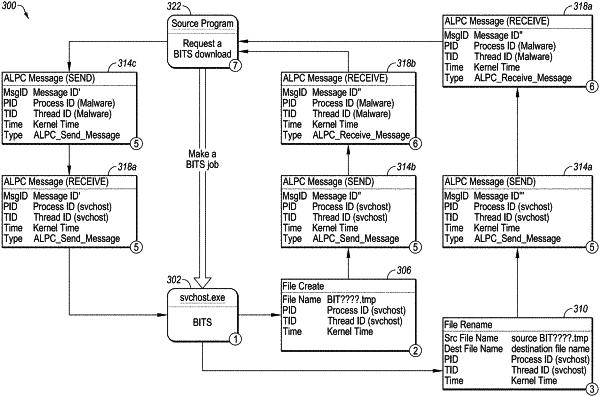
buffering, in a detection buffer within the memory, a plurality of send Advanced Local Procedure Call (ALPC) messages and a plurality of receive ALPC messages created by the operating system when a Background Intelligent Transfer Service (BITS) of the operating system is used to download one or more files to the computing device from a network;
identifying a first send ALPC message within the plurality of send ALPC messages and a first receive ALPC message within the plurality of receive ALPC messages, wherein the first send ALPC message and the first receive ALPC message have a first common message ID;
pairing the first send ALPC message and the first receive ALPC message to create a first ALPC message pair, wherein the first ALPC message pair includes:
a first timestamp field having a value corresponding to a time of creation of at least one of the first send ALPC message and the first receive ALPC message,
a first ALPC source process ID corresponding to a send process ID of the first send ALPC message,
a first ALPC source thread ID corresponding to a send thread ID of the first send ALPC message,
a first ALPC destination process ID corresponding to a receive process ID of the first receive ALPC message, and
a first ALPC destination thread ID corresponding to a receive thread ID of the first receive ALPC message;
receiving a notification that a temporary file has been created by the BITS, the temporary file created as part of a file download initiated by the source program;
determining that (1) the value in the first timestamp field corresponds to a time of creation of the temporary file, and (2) the first ALPC destination process ID corresponds to a process ID of the temporary file, and (3) the first ALPC destination thread ID corresponds to a thread ID of the temporary file;
evaluating the first ALPC source process ID to identify the source program responsible for initiating the creation of the temporary file;
determining, based at least in part on the temporary file, that the source program is a malware program; and
performing a security action on the source program.
|