| CPC G06F 21/40 (2013.01) [G06F 21/34 (2013.01); G06F 21/35 (2013.01); G06F 21/57 (2013.01); G06F 21/6218 (2013.01); H04L 9/0872 (2013.01); H04L 9/3215 (2013.01); H04L 9/3234 (2013.01); G06F 21/32 (2013.01); G06F 2221/0708 (2013.01); G06F 2221/2109 (2013.01); G06F 2221/2111 (2013.01); G06F 2221/2137 (2013.01); H04L 9/006 (2013.01); H04L 9/3213 (2013.01); H04W 12/67 (2021.01)] | 15 Claims |
|
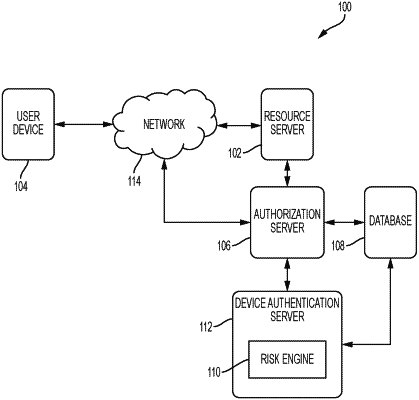
1. A method for providing an enhanced authentication process with risk-based decision making for accessing protected services, the method comprising:
capturing attributes pertaining to a user and/or a user device;
determining a risk of data security based on the attributes pertaining to the user and/or the user device;
when the risk is unacceptable, requiring additional authentication for access to the protected services; and
when the risk is acceptable, granting access to the protected services without requiring additional authentication;
providing an access token to the user device upon the granting access to the protected services, wherein the access token expires after a predetermined period of time; and
determining an updated risk of data security prior to a time expiration of the access token,
wherein the capturing the attributes pertaining to the user and/or the user device comprises:
performing an authorization call to an application requesting access to the protected services;
gathering the attributes while accessing the application; and
bundling the attributes and the request to access the protected services into an authentication request object that is created by an authentication software development kit (SDK) residing in the application.
|