| CPC G06F 9/45558 (2013.01) [G06F 11/1464 (2013.01); G06F 16/128 (2019.01); H04L 63/1416 (2013.01); H04L 63/1433 (2013.01); H04L 63/1441 (2013.01); G06F 2009/45562 (2013.01); G06F 2009/45583 (2013.01); G06F 2009/45587 (2013.01); G06F 2009/45591 (2013.01); G06F 2009/45595 (2013.01); G06F 2201/84 (2013.01)] | 23 Claims |
|
1. A method for securing virtual cloud assets against cyber vulnerabilities in a cloud computing environment, the method comprising:
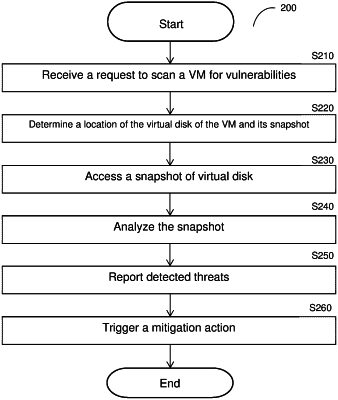
determining, using an API or service provided by the cloud computing environment, a location of a snapshot of at least one virtual disk of a protected virtual cloud asset, wherein the protected virtual cloud asset is instantiated in the cloud computing environment;
accessing, based on the determined location and using an API or service provided by the cloud computing environment, the snapshot of the virtual disk;
analyzing the snapshot of the at least one virtual disk by matching installed applications with applications on a known list of vulnerable applications;
determining, based on the matching, an existence of a plurality of potential cyber vulnerabilities;
correlating the determined potential cyber vulnerabilities with a network location of the protected virtual cloud asset;
using the determined plurality of potential cyber vulnerabilities and the network location of the protected virtual cloud asset to determine a risk of the protected virtual cloud asset to the cloud computing environment;
prioritizing, by the determined risk, the plurality of potential cyber vulnerabilities; and
reporting the determined plurality of potential cyber vulnerabilities as alerts prioritized according to the determined risk.
|