| CPC H04W 12/06 (2013.01) [H04W 12/04 (2013.01); H04W 12/40 (2021.01)] | 20 Claims |
|
1. An apparatus comprising:
at least one processor, at least one memory storing instructions that, when executed by the at least one processor, cause the apparatus at least to:
access to a first communication network, wherein the apparatus comprises a subscriber identity module configured for a second communication network, and wherein the second communication network is a legacy network with respect to the first communication network;
initiate an authentication procedure with at least one network entity of the first communication network and select an authentication method to be used during the authentication procedure, wherein the selected authentication method comprises a legacy authentication method of the second communication network; and
participate in the authentication procedure with the at least one network entity using the selected authentication method and, upon successful authentication, obtain a set of keys to enable the apparatus to access the first communication network;
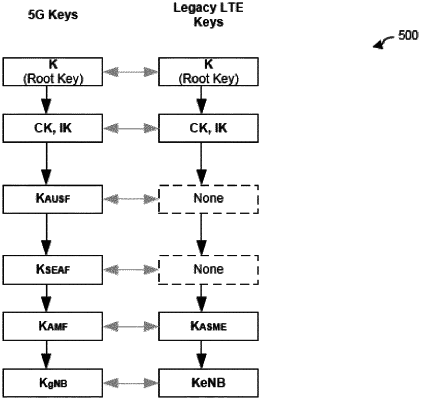
wherein the set of keys comprises one or more keys generated as part of the legacy authentication method of the second communication network which are used as at least a subset of the keys that would be generated as part of one or more authentication methods of the first communication network; and
wherein the one or more keys generated as part of the legacy authentication method of the second communication network are usable, as generated, in place of the keys that would be generated as part of the one or more authentication methods of the first communication network.
|