| CPC H04L 63/20 (2013.01) [H04L 41/145 (2013.01)] | 20 Claims |
|
1. A system to prevent multi-step security attacks, comprising:
a storage device; and
a processor in a network system communicatively coupled to the storage device, wherein the processor executes application code instructions that are stored in the storage device to cause the system to:
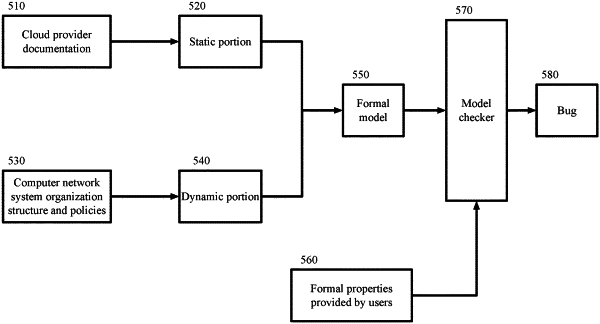
identify static and dynamic features of an identification and access management (“TAM”) system operated by a network computing system;
based on the static and dynamic features, create a formal model of the IAM system;
receive input of statuses of a simulated user into a Boolean solver based model checker that simulates users in the formal model, the status comprising at least a privilege status of the simulated user;
simulate, via the Boolean solver based model checker, every first action available to the simulated user, wherein at least one first action escalates the privilege status of the simulated user;
simulate, via the Boolean solver based model checker, every available subsequent course of action of the simulated user after the simulating of each of the first actions, wherein at least one of the subsequent courses of action is permitted based on the escalated privilege status;
determining that the privilege escalation leads to a security conflict; and
revise the static features or the dynamic features based on a determination that the privilege escalation leads to the security conflict.
|