| CPC H04L 63/20 (2013.01) [G06F 16/2455 (2019.01)] | 20 Claims |
|
1. A method comprising:
receiving, at a receiving module of a system on a chip (SoC), a packet;
determining a key identifying an inbound security association (SA) for the packet;
searching a hardware look-up table for the inbound SA of the packet based at least in part on the key;
determining the inbound SA of the packet based at least in part on the searching the hardware look-up table;
determining a corresponding SA memory address for the inbound SA;
providing the corresponding SA memory address for the inbound SA to an internet protocol (IP) security (IPsec) engine for processing of the packet with respect to an IPsec protocol;
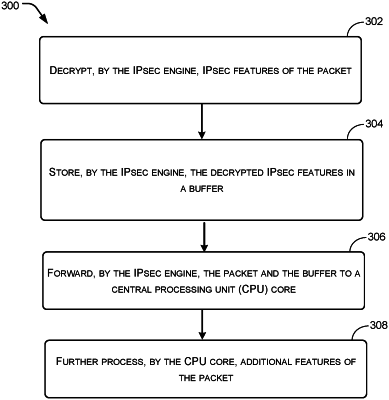
decrypting, by the IPsec engine, IPsec features of the packet;
storing, by the IPsec engine, decrypted IPsec features in a buffer;
forwarding, by the IPsec engine, the packet and the buffer to a central processing unit (CPU) core; and
further processing, by the CPU core, additional features of the packet, wherein during the further processing, the decrypted IPsec features are retrieved by the CPU core from the buffer,
wherein forwarding, by the IPsec engine, the packet and the buffer to the CPU core is based at least in part on a decrypted inner IP address of the packet and a classification related to the decrypted inner IP address of the packet in the hardware look-up table.
|